If you create an App Registration in Azure AD for a 3th party application you might want to limit the rights of this 3th party application.
For example you have a 3th party application which you want to access a specific mailbox to read mail from you would like to limit access to this specific mailbox only. To make sure that the application is not able to read the mailbox content of the CEO you need to implement an Application Access Policy.
Note: You need to have an Azure AD license to use Application Access policy’s.
First you need to create an App Registration for this 3th party application. Herefore follow the instructions from the 3th party app.
- Note the App ID of the 3th party app
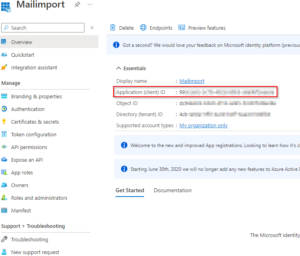
- Create Mail Enabled security group
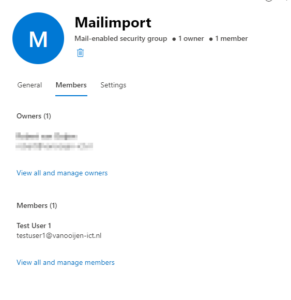
You will have to create a mail enabled security group. Members of this group will be the mailboxes which the application needs to have access to it.
- You can setup an Application Access Policy only through powershell. Use below script to create a Application Access Policy.
#Import Module Exchange Online and make connection to Exchange Online Import-Module ExchangeOnlineManagement Connect-ExchangeOnline #Variables $AppID = '[GUID APP ID]' $SecGroup = "mailimport@vanooijen-ict.nl" #Change to correct group name #Create Application Access Policy New-ApplicationAccessPolicy -AppId $appId -PolicyScopeGroupId $SecGroup -AccessRight RestrictAccess -Description "Application Access Policy for MailImport"
Change the variables so it will match your situation.
Outcome:

- Test Application Access Policy
You can test the outcome with the PS command:
Test-ApplicationAccessPolicy -Identity user@domain.nl -AppId $AppIDOutcome will show if access is granted or denied.

